The Gaming era has witnessed new gameplay when Mass effect was initially released back in 2007. It is the game with new concept and visuals, which changed the posibilities guidelines in the field.
Millions of gamers just love mass effects and how it is knitted along with the plot on which it has been released in series. Now that we are about to experience the ME3 very soon and most of us have white washed our gears to play the best of it, let us re-list the characters which actually facinates us.
Mass Effect 3 was released March 6, 2012 in North America, and will be released on March 8, 2012 in Australia and Switzerland, and March 9, 2012 in Europe.
Here are the list of top 10 Mass Effect Characters, which fascinates us (click on image to enlarge):
The Illusive Man claims that everything he does is for the benefit of humanity. However, his rocky past consisting of kidnapping, torturing, and unethically experimenting on humans seems to refute his great intentions. Behind each of The Illusive Man’s operations, there is a bigger picture that nobody but him can see. He always has an ace up his sleeve, which inevitably leads to another conspiracy. The Illusive Man is one of the more perplexing characters in the Mass Effect universe and we can’t wait to find out more about him in the final chapter of the trilogy.
Thane is a deeply religious Drell and this strongly contrasts with his career choice as a professional hitman. Thane has tried to convince himself that living life as an assassin is not a sin, because he believes the body and the soul are two separate entities. However, the Drell species’ ability to relive memories in perfect detail constantly reminds Thane of his acts of violence causing him to sort through much hardship. Thane also contradicts himself when he learns his son is following in his footsteps. Thane is completely against this, hinting that the Drell father is ashamed of his work as well. Thane is a wonderfully interesting character, earning him the No. 2 spot on our list.
Grunt is a particularly interesting character, because of all the ethical dilemmas surrounding his creation. Grunt essentially shares the same creation story as Miranda, since both characters were born as genetically engineered elite members of the species. Grunt is different though, as he was created to be a natural warrior and constantly has the driving force to kill something. Grunt struggles with calming this drive to kill, because he knows it is wrong and he knows it is unnatural. At the same time, Grunt also deals with identity issues.
Nothing is more exciting than making a decision, while assuming the role of Commander Shepard. Sure, shooting your way through a space station is awesome, and nothing takes away from using biotics to lift and throw your enemies. But when it comes down to it, making a story-altering decision with unknown consequences is the reason why we love being Commander Shepard. Would Shepard kill the Rachni Queen? Would Shepard save the Collector base? Would Shepard save the Council? That depends on who the player behind the Shepard is, and that is what makes the Commander such a great character.
Seated at the top of the biggest organized crime racket, the Shadow Broker is a natural and unbiased capitalist, selling information to the highest bidder. The Shadow Broker doesn’t care who his buyer is, nor does he care about what he is selling them or what the consequences might be for doing so. During the “Lair of the Shadow Broker” DLC, the Shadow Broker’s identity is revealed. The Shadow Broker was a member of the Yahg race, a species deemed too dangerous and power-hungry by the Citadel Council. Once an agent for the previous Shadow Broker, this Yahg killed him and resumed the role for another six decades.
 6. Jack: Jack has the most depressing back-story of anybody in the Mass Effect universe. Kidnapped by Cerberus at age 4, the human terrorist organization experimented on her daily. Jack was locked in a cell and made to believe that the only world outside of her cell was what she could see from a small window. Unbeknownst to Jack, this window was actually a one-way mirror used to observe her. Commander Shepard recruited Jack, although any true emotional connection seems to be impossible. There has been too much deceit and pain in her life to trust somebody ever again.
6. Jack: Jack has the most depressing back-story of anybody in the Mass Effect universe. Kidnapped by Cerberus at age 4, the human terrorist organization experimented on her daily. Jack was locked in a cell and made to believe that the only world outside of her cell was what she could see from a small window. Unbeknownst to Jack, this window was actually a one-way mirror used to observe her. Commander Shepard recruited Jack, although any true emotional connection seems to be impossible. There has been too much deceit and pain in her life to trust somebody ever again.
Captain Kirrahe had, without a doubt, the single best speech in the original Mass Effect script. For some reason, the writers of Mass Effect decided to ignore the main cast of characters and give this amazing monologue to a character the player had only just briefly met. Regardless, what a great first impression. Kirrahe’s speech to a less-than-confident squad on Virmire is enough to raise the hair on your arms. “Our influence stopped the Rachni, but before that we held the line! Our influence stopped the Krogan, but before that we held the line! Our influence will stop Saren. In battle today, we will hold the line!”
Mordin is a great character because of his interesting set of morals alongside a unique way of communicating. Salarians only have an average lifespan of 40 years, so everything they say is fast and everything they say has a purpose. The Salarians are also very interested in technology and the advancement of their species, which explains why Mordin’s philosophy is logic and statistics and less about emotions and feelings. “ Mordin and his fellow Salarian scientists decided to create the Genophage, because they felt the Krogan Rebellions put the galaxy in jeopardy. They decided in order to preserve the natural balance of things, the Krogans must be eliminated, which lead to the Genophage.
Wrex, an infamous Krogan Battlemaster, leaves a trail of destruction where ever he goes. Wrex is a beloved character because no matter the person, he’ll always find a flaw that justifies killing them. In this way, he is as blackly humorous as he is interesting. His first solution to every problem seems to be focused around violence and given everybody else’s diplomatic attitudes in the first Mass Effect, this was sorely needed. It was also great to see him calm down in Mass Effect 2 and begin preparations to save his species. A focus on breeding is emphasized in his community in order to combat the Genophage and restore the Krogan population. That is, if you didn’t shoot him.
 10. Captain David Anderson: The David Palmer of the Mass Effect universe, Captain David Anderson is the voice of reason in the face of dire circumstances. Not afraid to state his opinion, Anderson argues for the continued investigation of the Reapers, while always presenting his case for the equal treatment of humanity. Captain Anderson is respected by everybody and his commitment to saving human lives surpasses his own need to survive. It is these admirable traits that earned Captain Anderson a spot on our list.
10. Captain David Anderson: The David Palmer of the Mass Effect universe, Captain David Anderson is the voice of reason in the face of dire circumstances. Not afraid to state his opinion, Anderson argues for the continued investigation of the Reapers, while always presenting his case for the equal treatment of humanity. Captain Anderson is respected by everybody and his commitment to saving human lives surpasses his own need to survive. It is these admirable traits that earned Captain Anderson a spot on our list.
[viaplanetxbox360]








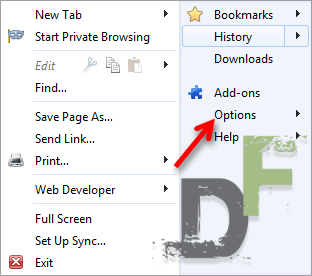
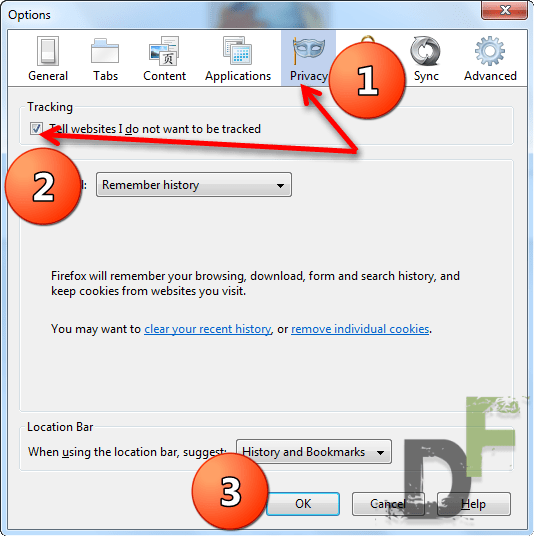
![[How to] Enable “Do Not Track” on Mozilla Firefox](https://digitfreak.com/wp-content/uploads/2012/02/mozilla-do-not-track-1.png)
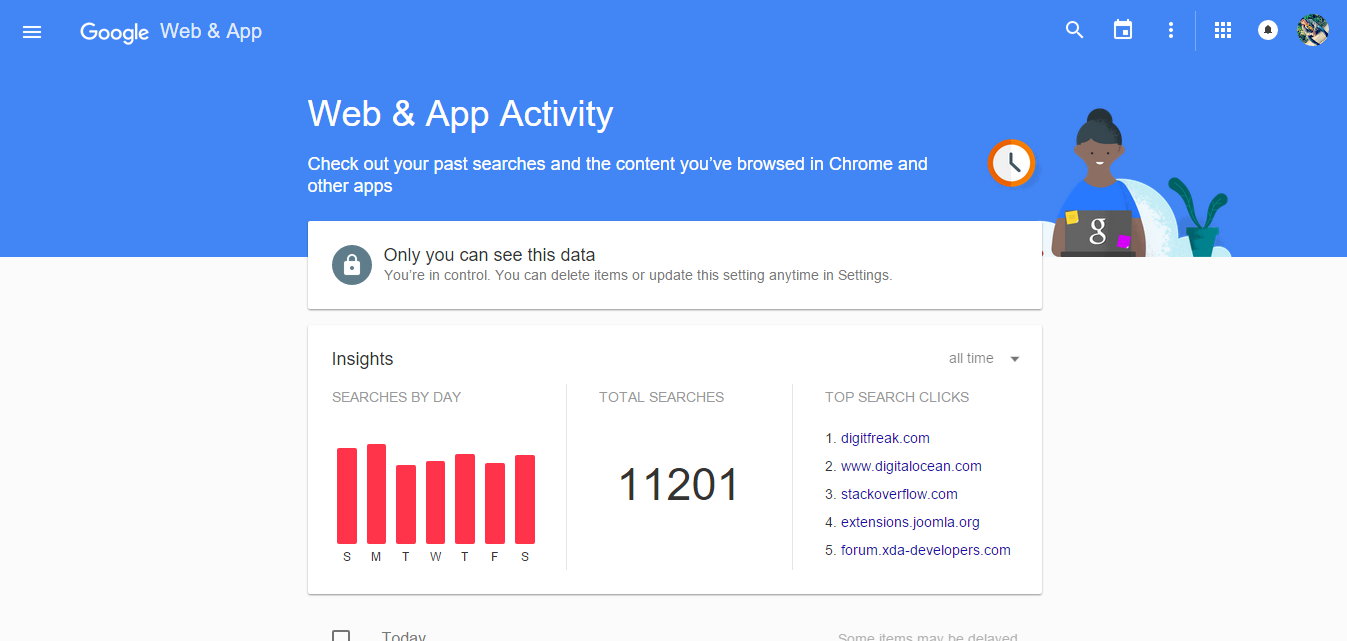
![[How to] Wipe Google Search activity history from your account](https://digitfreak.com/wp-content/uploads/2012/02/z_digitfreak_00401.jpg)
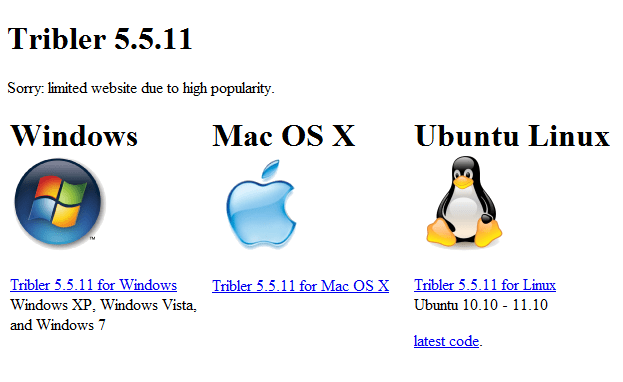
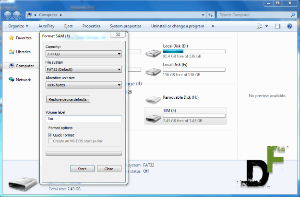
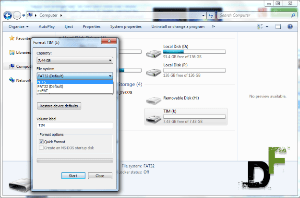
![How to make a bootable Windows USB anytime! [windows and ubuntu platforms]](https://digitfreak.com/wp-content/uploads/2012/02/thumb_windows 1.png)
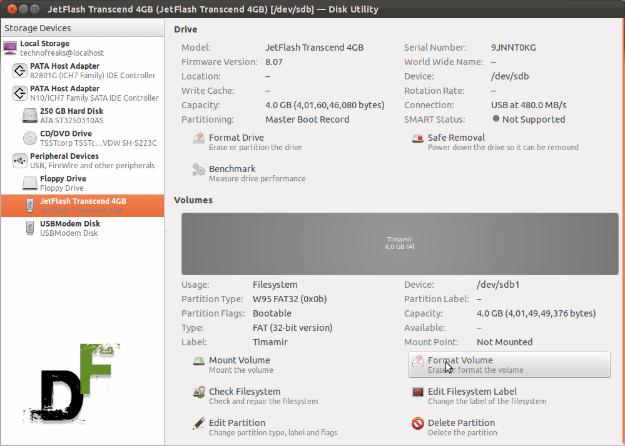
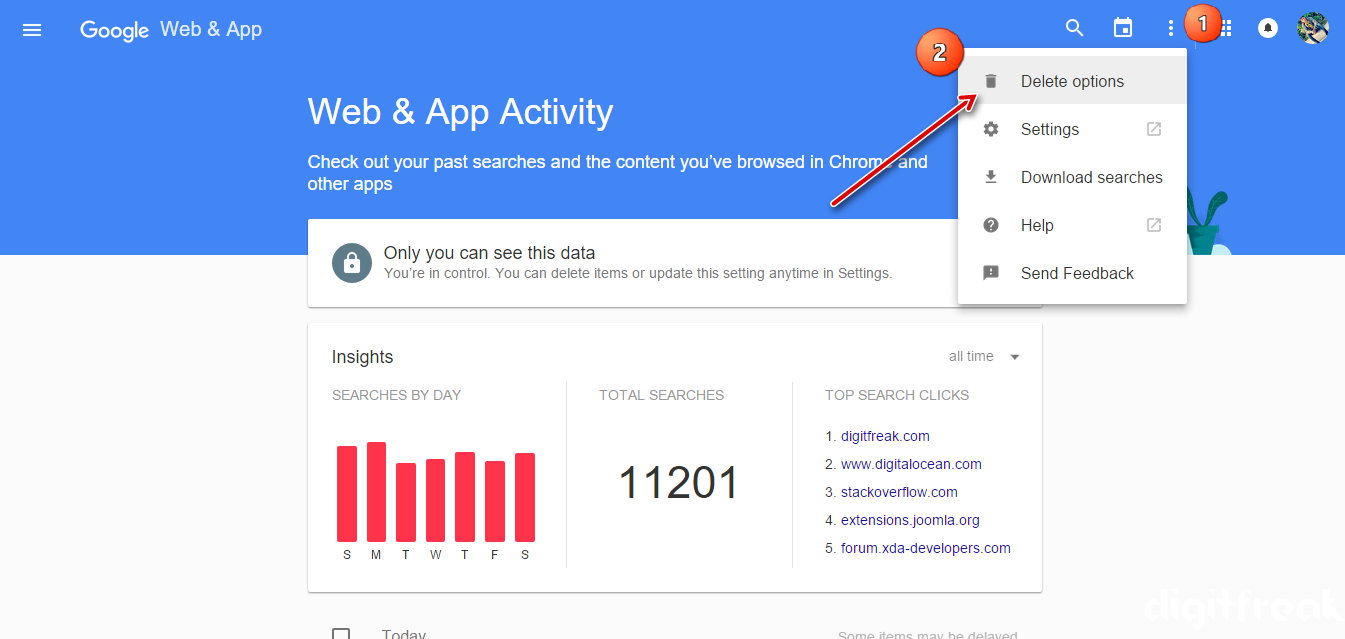
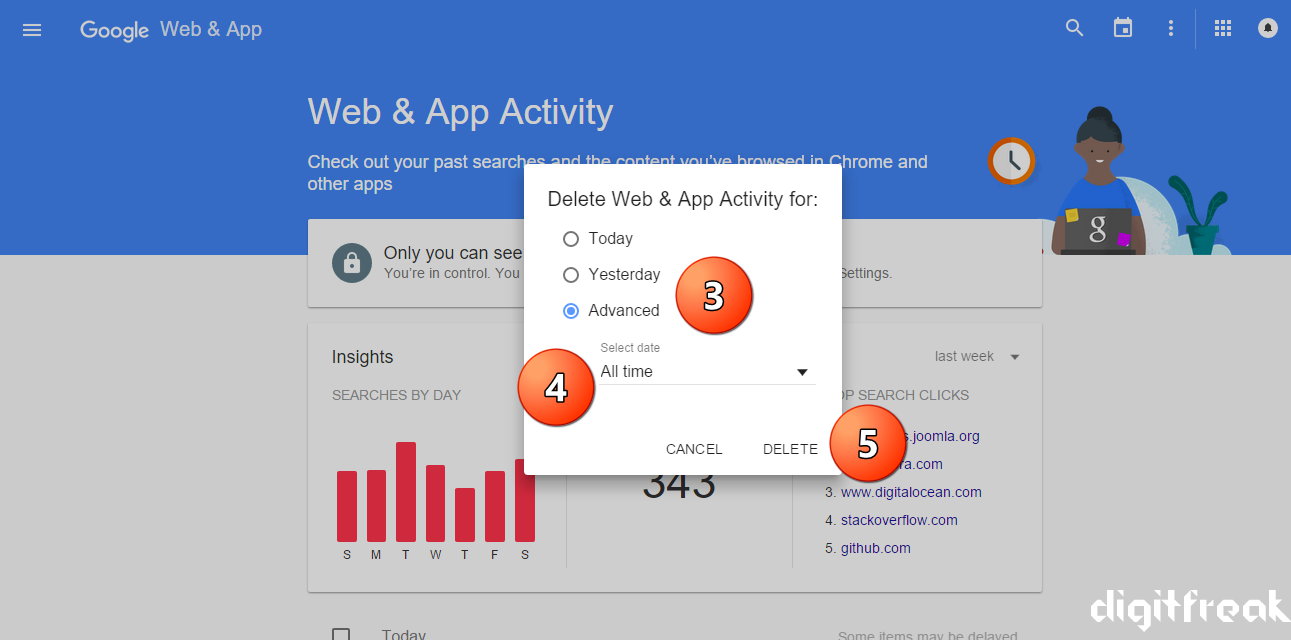
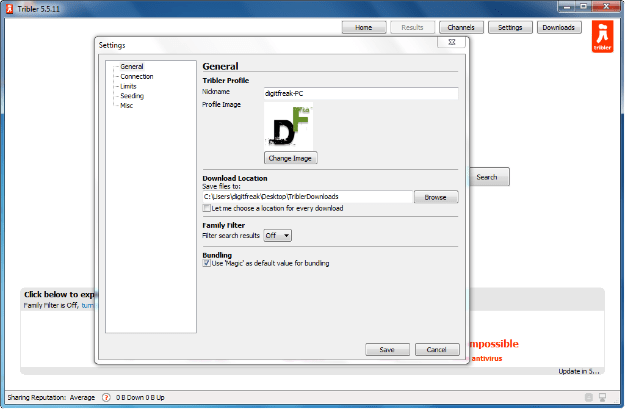 The “settings” windows offers very basic and useful option which could be helpful while using the client. It is the place where you can add your user profile and enjoy online identity.
The “settings” windows offers very basic and useful option which could be helpful while using the client. It is the place where you can add your user profile and enjoy online identity.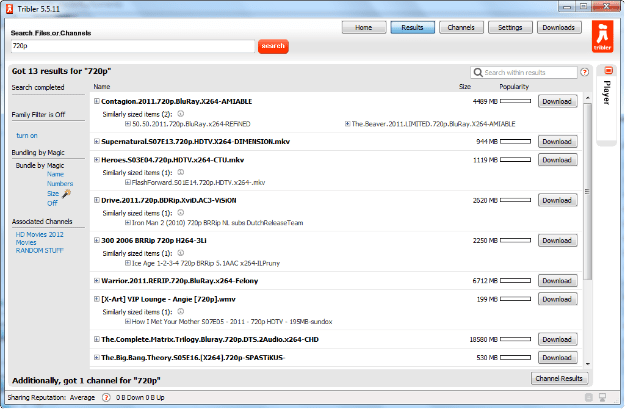 Tribler offers search listing of your queries which works on different mechanism of other torrent websites. It doesn’t relies on the centralized server to perform its queries, rather it can retrieve the data and .torrent files from other peers connected to your client. To get the most relevant and most relevant result you must keep your client running for at least 5 minutes before performing the search query, as the client connects to other peers and maintains an index while it is running, which can further help you get the most relevant search results of your desired destination.
Tribler offers search listing of your queries which works on different mechanism of other torrent websites. It doesn’t relies on the centralized server to perform its queries, rather it can retrieve the data and .torrent files from other peers connected to your client. To get the most relevant and most relevant result you must keep your client running for at least 5 minutes before performing the search query, as the client connects to other peers and maintains an index while it is running, which can further help you get the most relevant search results of your desired destination.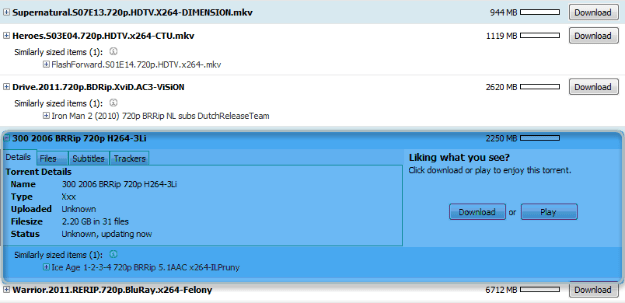 The download process if very easy and is performed on the fly, downloading a torrent file was never so easy. You just need to click on the name of the file you want to download in your search results and information related to the file will slide in right below the name, where you can find all the relevant information about the file right inside your client. You’ll find download button after each filename, clicking on which download starts automatically and tribler will download .torrent meta file from other peer on the network and start your download.
The download process if very easy and is performed on the fly, downloading a torrent file was never so easy. You just need to click on the name of the file you want to download in your search results and information related to the file will slide in right below the name, where you can find all the relevant information about the file right inside your client. You’ll find download button after each filename, clicking on which download starts automatically and tribler will download .torrent meta file from other peer on the network and start your download.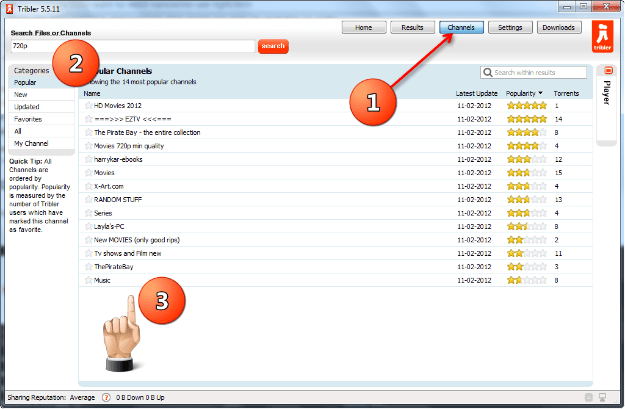 This is the features, which makes me happy. It is not much of the useful thing atm, but soon, when other users will start listing the torrent files which they find useful for them on their own profile, it will be the best thing on the client or any other p2p software out there.
This is the features, which makes me happy. It is not much of the useful thing atm, but soon, when other users will start listing the torrent files which they find useful for them on their own profile, it will be the best thing on the client or any other p2p software out there. 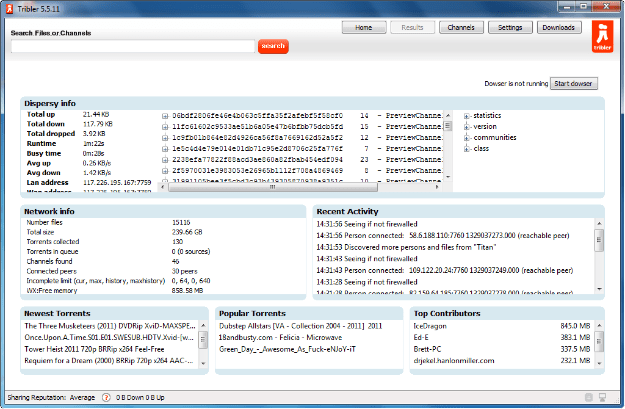 Like many other BitTorrent clients, Tribler has a search box at the top of the application. However, the search results that appear when users type in a keyword don’t come from a central index. Instead, they come directly from other peers.
Like many other BitTorrent clients, Tribler has a search box at the top of the application. However, the search results that appear when users type in a keyword don’t come from a central index. Instead, they come directly from other peers.