Spamhaus has been a quite a buzz recently on the internet – and it should be. It faced a biggest DDoS attack reported so far on the internet and successfully mitigated it. The whole process to keep the site alive, couldn’t be possible without CloudFlare (the cloud computing service, which powers our website too).
At the very beginning of the attack, it noted as an average DDoS attack, ranging from 80-90 Gbps of traffic – which could be easily pulled down. But, as time went by it got worse. Cloudflare took command when Spamhaus knocked on their doors and everything was managed in a proper way with vital resources available.
 Cloudflare wrote on their blog:
Cloudflare wrote on their blog:
The attackers were quiet for a day. Then, on March 22 at 18:00 UTC, the attack resumed, peaking at 120Gbps of traffic hitting our network. As we discussed in the previous blog post, CloudFlare uses Anycast technology which spreads the load of a distributed attack across all our data centers. This allowed us to mitigate the attack without it affecting Spamhaus or any of our other customers. The attackers ceased their attack against the Spamhaus website four hours after it started.
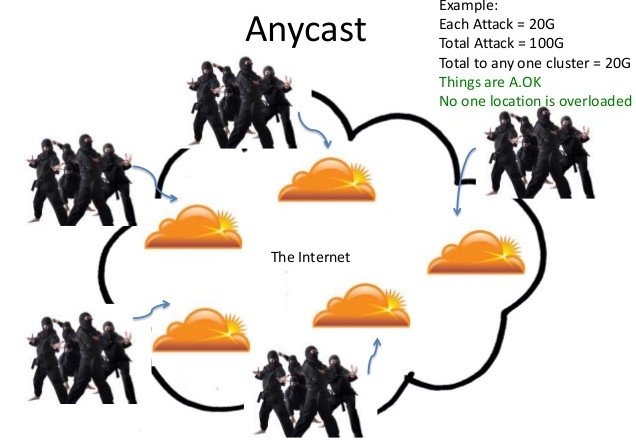 When the attackers couldn’t take down Spamhaus (thanks! to anycast technology used by CloudFlare), they changed their tactics. First the CloudFlare’s bandwidth providers were attacked and then it took the bigger frame – Tier 2 providers.
When the attackers couldn’t take down Spamhaus (thanks! to anycast technology used by CloudFlare), they changed their tactics. First the CloudFlare’s bandwidth providers were attacked and then it took the bigger frame – Tier 2 providers.
The “inter” in Internet refers to the fact that it is a collection of independent networks connected together. CloudFlare runs a network, Google runs a network, and bandwidth providers like Level3, AT&T, and Cogent run networks. These networks then interconnect through what are known as peering relationships.
When you surf the web, your browser sends and receives packets of information. These packets are sent from one network to another. You can see this by running a traceroute. Here’s DigitFreak’s individual traceroute :
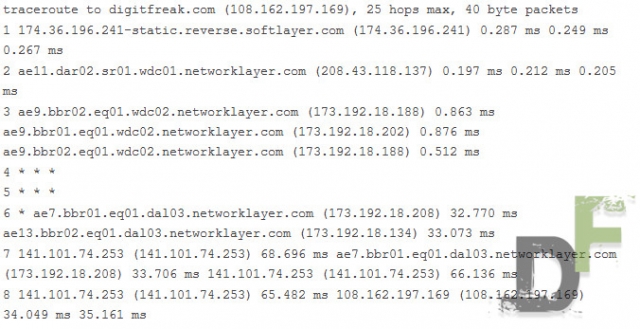 Once the attackers realized that they cannot take CloudFlare with 100 Gbps+ DDos Attack, they immediately started attacking Tier2 bandwidth providers – which started congesting Tier 1 bandwidth provider (Tier 2 bandwidth providers buy bandwidth from Tier1, who are actually responsible for generating the internet bandwidth. So basically Tier1 providers are the one who makes sure that internet is never knocked down by engaging bandwidth).
Once the attackers realized that they cannot take CloudFlare with 100 Gbps+ DDos Attack, they immediately started attacking Tier2 bandwidth providers – which started congesting Tier 1 bandwidth provider (Tier 2 bandwidth providers buy bandwidth from Tier1, who are actually responsible for generating the internet bandwidth. So basically Tier1 providers are the one who makes sure that internet is never knocked down by engaging bandwidth).
One of the Tier 1 provider reported Cloudflare that they are receiving 300Gbps+ of traffic related to Spamhaus attack – which makes it largest reported DDoS attack in the history.
The number of open DNS resolvers is dropping—CloudFlare reported that it was down by about 30 percent in February—but they’re still abundant, and as the current attacks on SpamHaus make clear, still enough to be tremendously problematic.
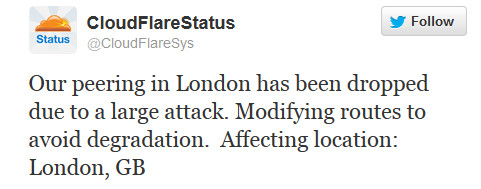 The attacked also attacked Internet Exchanges (IXs), which helps CloudFlare connect with other networks. These IXs are responsible for connecting the multiple networks as basic level switches and can pass bandwidth over the network. It is very critical infrastructure in Europe which connects largest networks including CloudFlare, Google, Facebook and just about every other major internet company.
The attacked also attacked Internet Exchanges (IXs), which helps CloudFlare connect with other networks. These IXs are responsible for connecting the multiple networks as basic level switches and can pass bandwidth over the network. It is very critical infrastructure in Europe which connects largest networks including CloudFlare, Google, Facebook and just about every other major internet company.
If you are our regular follower – you must have read the blog post, where we told you about the DDoS attack we faced earlier. CloudFlare helped us mitigate the attack quickly then.
Cloudflare’s AnyCast technology distributed the traffic to their mirror cloud servers and the load was balanced evenly to the network – making the attack less vulnerable.
Cloudflare Further writes on their blog:
At the bottom of this attack we once again find the problem of open DNS recursors. The attackers were able to generate more than 300Gbps of traffic likely with a network of their own that only had access 1/100th of that amount of traffic themselves. We’ve written about how these mis-configured DNS recursors as a bomb waiting to go off that literally threatens the stability of the Internet itself. We’ve now seen an attack that begins to illustrate the full extent of the problem.
Unlike tradition DDoS attack simulation which is carried on connection of home PCs or modest Internet connection, these attacks were being carried on big servers with fat pipes. They can be literally called bazookas which could have damaged the entire Internet.
According to ArsTechnicia, CyberBunker is the originating server of the attack:
It now seems that the attack is being orchestrated by a Dutch hosting company called CyberBunker. CyberBunker specializes in “anything goes” hosting, using servers in a former nuclear bunker (hence the name). As long as it’s not “child porn and anything related to terrorism,” CyberBunker will host it. This includes sending spam.
The attackers never succeed to bring down Spamhaus, CloudFlare or Internet as a whole. Everything settled peacefully without having much damage. This couldn’t be possible without CloudFlare being involved in the attack.
CloudFlare proved that they are something which could be trusted on and can be reliable when it comes to the network attacks. They understand it best.
What do you think? Let us Know.
Leave a Reply