A new security bug targeted to Android devices allows anyone to spy on anyone with single MMS (video message). What makes it even scary is that the attacker don’t even require your interaction with the message sent to your device. You just have to look at the notification or unlock your device when such message arrives on your phone. Isn’t it scary?!
What is it?
It is theoretically a security bug in Android system that penetrates almost all smartphones powered by Android ecosystem. Devices that run Android OS older than Jelly Bean 4.1 are at high risk because they lack the application sandbox design to protect user data and other applications on the device.
The security of Android users is extremely important to us and so we responded quickly and patches have already been provided to partners that can be applied to any device.
Most Android devices, including all newer devices, have multiple technologies that are designed to make exploitation more difficult. Android devices also include an application sandbox designed to protect user data and other applications on the device. — said Google
The detailed information has not been made public yet, which is highly likely to be revealed during the upcoming Black Hat conference next week in Las Vegas. All we know right now that your Android phone can be tracked, monitored or exploited for some serious cyber crime if you do not take precautions or keep your device updated.

The exploit comes into play with Google’s “stagefright” media playback engine, which was introduced in Android 2.2 and prevailed ever since. It was only recently exploited when Google hangout and other 3rd party SMS apps introduced the feature to autoplay MMS (text message) on the phone once the user opens the message or notification.
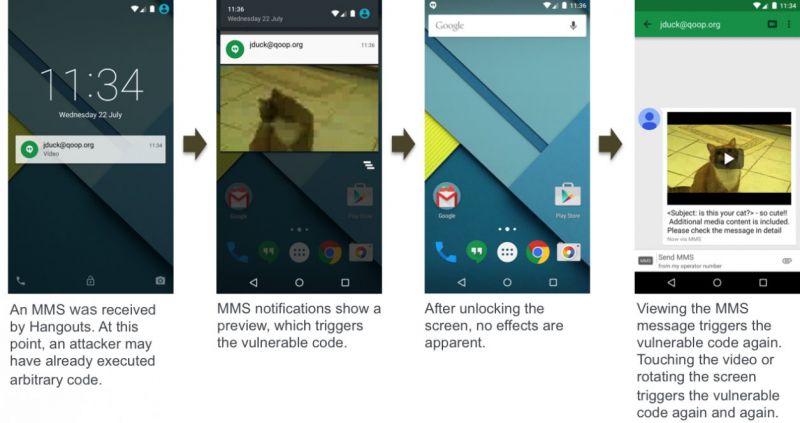
The security hole affects almost all versions of Android, from version 2.2 right up to 5.1, the latest version. An Android user simply needs to receive a text message (MMS) from the attacker, which automatically trigger the malicious code hidden in that video message (thanks to the stagefright). This code can then be triggered when you see the notification, unlock screen to see the message, and finally when you watch the MMS message, touch the video or rotate the screen.
The good news is that Google has already developed a patch for this vulnerability and it is ready to be deployed through OTA — but, only if you have Google Nexus devices. For everyone else, you will have to rely on your manufacturer or service provider to roll out the security patch that would eventually fix this bug.
How to Keep your device safe?
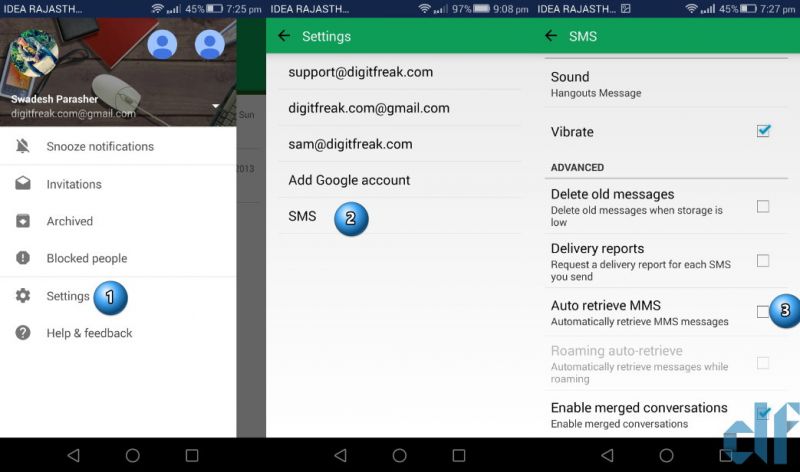
Image courtesy: Swadesh Parasher
If you use Google hangout to manage text messages on your device, the fix is really easy.
- Open Google Hangout App > Go to “Settings”
- Go to “SMS” option.
- Scroll down, and un-check “Auto retrieve MMS”
That’s it! it will protect you from the automatic execution of malicious code on your device when you receive an MMS message from your attacker. However, you can still get infected if you open the video or play it on your device. There’s nothing much you can do except taking precautions and be careful when you receive the MMS (Who uses it today?) from an unknown number.
All other third party SMS apps may or may not have the option to turn off auto retrieve function of MMS, if that is the case we suggest you use any other SMS managing app from play store that allows you to turn off MMS feature completely. If you’re a root user simply remove the third party apk files from your phone and keep your device up to date.
Source: TheRegister
Leave a Reply