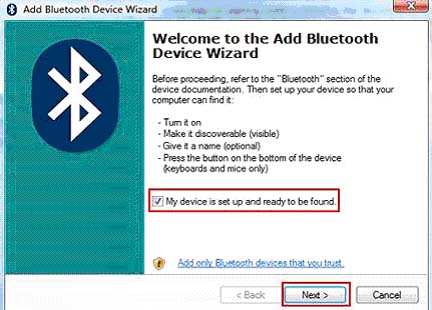
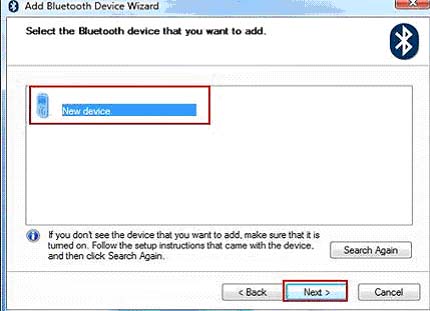
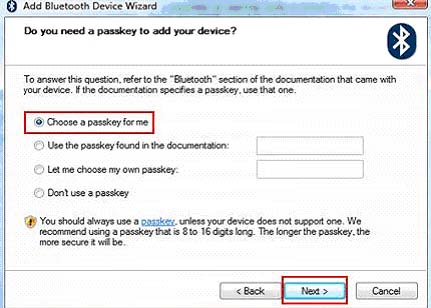
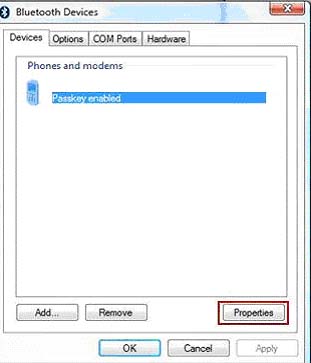
Give your internet browser instant amnesia with these quick tricks. A lot of these tactics make surfing faster and safer, too.
Cache out
Back in the bad old days of dial-up internet, web browsers tried to be helpful and speed up browsing by downloading and storing a cached copy of the web pages we visited, since calling up that information from our hard drives was a lot faster than downloading it every time we went to one of our favorite sites. Now, with the
widespread availability of fast internet connections, this cache of temporary internet files is more like our browsing software’s appendix than a must-have feature.
Deleting these files when your browser closes, rather than letting them hang around, is definitely a good idea if you don’t want your computer — and anyone who happens to sit down at it — to know where you’ve been. Internet Explorer lets you do this automatically when the browser exits; Firefox, Safari, and Chrome all require you to delete these files by hand (though there are extensions for bothChrome and Firefox that let you automate the process).
Don’t know much about history
So, we’ve dumped out the temporary files that your computer has downloaded — but that’s only part of the solution. Your browser still remembers what pages you’ve been to (called the browsing history), a convenience that allows your browser to populate the address bar after you’ve only typed a few letters of the web address. However, by clicking the down arrow at the edge of the address bar, anyone can see at a glance a whole bunch of recent web destinations that browser has been to. Not exactly the way to keep a low profile if you’re doing some holiday shopping or job hunting on company time, to say the least.
Deleting your history purges this information from your browser’s memory (since it persists from one browsing session to the next, even if you purge your temp files).
Cookie monsters
Cookies, those tiny text files that let web pages know you’ve visited them before, are the third part of the equation. Their entire reason for being is to identify you and track your web habits when it comes to being a regular at a website, whether it’s Amazon or Facebook or Gmail. Tossing your cookies will allow you to visit websites as if you’d never been there before. Anyone snooping on your computer after you’ve cleared the cookies away won’t see their telltale leavings, even if the cookies themselves don’t contain anything but site addresses and the dates and times of your last visit.
When convenience gets inconvenient
Finally, there’s the matter of web browsers storing usernames, passwords, and other form data for sites you visit that require a username to log in. This information is a time-saver when you’ve got a million passwords to remember, but it can also be an Achilles’ heel if you’re trying to be stealthy about your web travels.
If someone else sits down at your computer to check email on the same webmail service you use, it’s far too easy for browsers to auto-fill the login fields with your username (and maybe even a password), so this is something you may want to scrub from time to time, too. After all, it’s one thing for somebody to glance at your web history and something else altogether if up comes your email inbox!
Private eyes
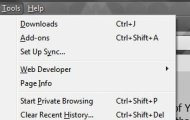
All of the current crop of internet browsers include a feature that lets you in effect surf off the record. The programs themselves will empty the cache and delete the browsing history when you finish; they won’t load any add-ons, and they’ll ignore website requests to store cookies.
No matter which of the major browsers you use, visit the Tools menu (or select the gear- or wrench-shaped icon that serves the same purpose) to choose to start a Teflon-coated browsing session, usually in a new window. The upside of explicitly opening a private browsing window is that it doesn’t inconvenience you by deleting your history, cookies, and any stored logins you normally use, while still cloaking what you do in that window from prying eyes.
There are plenty of reasons why you might want to use private, no-traces-left-behind surfing sessions, like planning a surprise getaway for you and your partner or keeping tech-savvy youngsters from knowing where you’ve been shopping for their birthday present.