Netizens have a handful of options to protect their Privacy over the internet, and security experts also recommend practicing the standard protocols to prevent identity theft and security breach. Many of us are ready to implement these security layers to our system, but the main issue is that they are not always free or affordable.
A secure router like ‘bitdefender box‘ can provide highly secured communication line to all the wireless devices that are connected to it, but currently it is only available in US and costs $199. There are premium VPN services that can provide similar protection over multiple devices, such as hideipVPN, CactusVPN, VPN4ALL, VyprVPN etc. Then there are DNS services like Unotelly, which are capable of lifting the restriction from geo-blocked websites. We also covered the basics of wireless security earlier, which gives you a good idea how to protect yourself from the interception of wireless traffic.
All of these options are highly recommended and secure way to access the internet, but if you’re like me who just wants to access the geo-blocked websites while keeping the identity private, these “Free” Google Chrome extensions will get you going.
The recent melodramatic event in India, where the government took a major decision to block more than 800 porn websites in the country sparked outrage. Free porn websites, including Pornhub.com, xvideos.com, playboy.com and xxx.com are blocked by ISPs in India and many other countries. These restriction imposed by the Indian government was ordered to be lifted, ruling out the previous decision, but ISPs choose not to unblock these websites to this date.
One should always keep a handy note of these free Chrome VPN tools to bypass the restriction on content accessibility.
Here are some Free Google Chrome VPN extensions to unblock almost any website:
ZenMate
This is probably the best free VPN service, that provides unlimited usage without any logical limitations. Of course you are limited to the number of server locations you can use, which includes US, Romania, Germany and HongKong. We tested Zenmate to unblock some website which are currently being blocked by my ISP, and it perfectly lifted restrictions. We were actually amazed because we could stream videos and other heavy contents over this secure network, like there was nothing in between, throttling the speed.
When we tested Zenmate for DNS leak, it returned the owner as “Hurricane Electric,” which apparently is a global internet service provider. So we can vouch that it does pretty good work at hiding your information unless zenmate or Hurricane is keeping your activity records.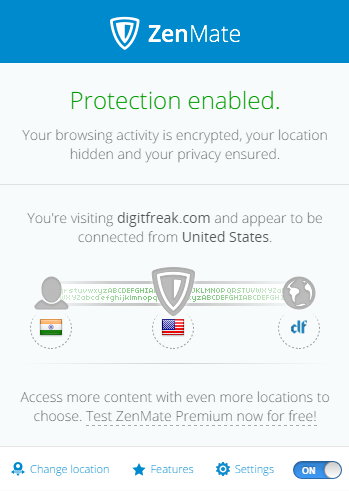
Zenmate is available for cross-platforms, which includes Google Chrome, Mozilla Firefox, Opera, Android, and iOS. If you like their free chrome extension, you can even try premium plans which can protect all your devices over the network.
[Download]
Unlimited Free VPN – Betternet

The only reason we are not listing this service at the top, it is a comparitively new company. The service is open source, and completely free. It is the only free VPN service we know that doesn’t sell you ads or offers alternate premium plans to bump up the speed or data usage. It is FREE 100%, with the only drawback being available 1 US server location which cannot be changed.
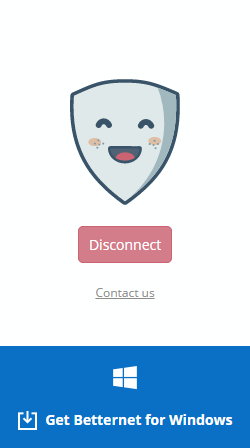
We love how they disclose their monthly earning from the apps they recommend under the partnership with third party networks. Betternet is available for all the platforms – Mozilla Firefox, Google Chrome, Windows, Android, and iOS.
[Download]
CyberGhost
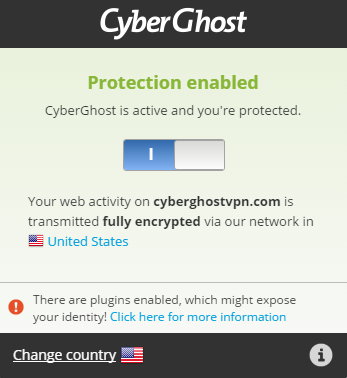
CyberGhost is a reputed VPN company, which proved to be a good tool to unblock banned websites by their free Google Chrome extension. It is a company recognized by many reputed tech blogs — wired, TechCrunch, the guardian and chip to name a few. It is a big name and very trusted.
We liked the simple UI, and limited options to play with. It offers 3 server locations – United States, Germany and Netherlands which cannot be extended by a premium service unless you happen to vouch for a paid VPN account that protects entire network on your computer.
There is a dedicated free Android app, but it didn’t perform quite well during our test. Maybe it was some glitch at their end during that session.
[Download]
We also tested ultrasurf, Gom VPN, dotVPN, Unlimited Free VPN – Hola and TunnelBear — they were offering either limited bandwidth and required registration or leaked DNS information and forced advertisements, which isn’t good if you wanted to hide your online identity.
These tools are highly effective and we tested them for DNS and information leaks, but keep in mind that they are not as secure as a reputed premium VPN services and are not recommended for those who are seeking top-notch security.
Most of these services might be keeping activity logs. The owners of the services above have the ability to associate your personal IP address with the names of all the sites you connect to and store this data indefinitely, which can identify you if authorized personnel to contact them for investigation of your involvement in a suspicious activity. This does not mean that they do log or store it indefinitely but they may and you need to trust whatever their policy says.

